Comparing M2M Protocols: MQTT vs. CoAP in IoT Applications
Introduction
The Internet of Things (IoT) has revolutionized the way devices interact and communicate, leading to the rise of Machine-to-Machine (M2M) protocols. These protocols play a crucial role in establishing seamless connections between IoT devices, enabling them to share data, control actions, and collaborate effectively. Two prominent M2M protocols, MQTT (Message Queuing Telemetry Transport) and CoAP (Constrained Application Protocol), have emerged as popular choices for IoT applications. In this article, we delve into the intricacies of MQTT and CoAP, comparing their features, use cases, and performance to help IoT developers and engineers make informed decisions when choosing the most suitable protocol for their projects.
MQTT vs. CoAP:-
Understanding MQTT
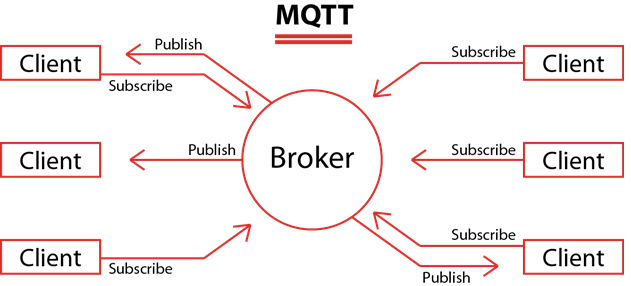
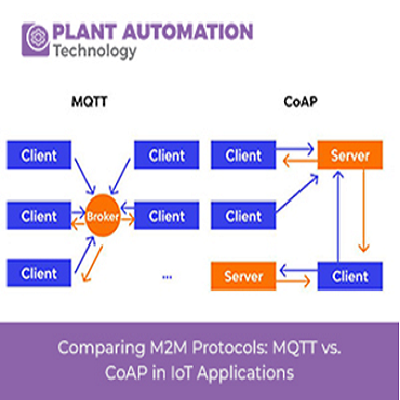
MQTT, originally developed by IBM, is an open-standard, lightweight, and simple messaging protocol designed for machine-to-machine communication. At its core, MQTT follows a publish-subscribe messaging pattern, where devices called publishers send messages to a central broker. These messages are then distributed to devices called subscribers, which are interested in receiving the data.
MQTT's architecture makes it an excellent choice for various IoT applications. Its lightweight design and low overhead are ideal for constrained devices with limited processing power and memory. MQTT minimizes the use of bandwidth, making it suitable for scenarios with low connectivity or high latency, such as remote and rural deployments. Additionally, MQTT's QoS (Quality of Service) levels offer different message delivery guarantees, allowing developers to prioritize message delivery based on their application requirements.
MQTT uses a simple binary message format that consists of a topic and a payload. The topic acts as a hierarchical address, and the payload carries the actual data. This format ensures efficient data exchange between devices without unnecessary data parsing overhead. Moreover, MQTT's small code footprint makes it well-suited for microcontrollers and resource-constrained devices.
One of MQTT's primary strengths is its wide adoption and robust community support. This popularity has led to the development of various MQTT libraries and client implementations across multiple programming languages and platforms. This extensive support simplifies the integration of MQTT into different IoT ecosystems and frameworks.
Exploring CoAP
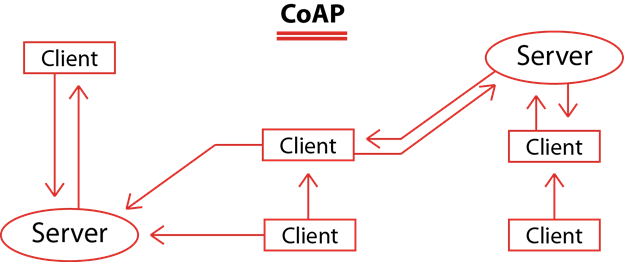
CoAP, on the other hand, stands for Constrained Application Protocol and was specifically designed for constrained devices in low-power and lossy networks. It follows a request-response model, similar to HTTP, allowing devices to perform operations like GET, PUT, POST, and DELETE on resources represented by URIs.
CoAP's design philosophy is centered around providing a lightweight communication protocol that can efficiently run on constrained devices, such as wireless sensor nodes and IoT devices with limited resources. Unlike MQTT, CoAP is based on the UDP transport protocol, which reduces the overhead of connection establishment and data exchange. This makes CoAP an energy-efficient choice, well-suited for battery-operated IoT devices and networks.
CoAP incorporates features like multicast support and built-in caching for efficient resource discovery and management. The multicast capability allows a single CoAP message to be sent to multiple devices simultaneously, which is beneficial in scenarios where multiple devices require the same data. Additionally, CoAP's caching mechanism helps reduce redundant requests, conserving valuable network resources and lowering latency.
CoAP supports four reliability modes for messages: Confirmable, Non-confirmable, Acknowledgment, and Reset. These modes allow developers to prioritize message reliability based on their application's requirements. CoAP's reliability options strike a balance between ensuring message delivery and minimizing overhead, making it an excellent choice for various IoT scenarios.
MQTT vs CoAP in IoT
|
MQTT |
CoAP |
|
In this model, the primary participants are publishers and subscribers. |
It utilizes request and response interactions. |
|
Central broker optimally routes messages from publishers to clients. |
Message dispatching occurs on a one-to-one basis, similar to HTTP. |
|
Event-oriented operations |
Viable for state transfer |
|
Establishing a continual and long-lasting TCP connection with the broker is essential for the client. |
Involved parties use UDP packets (async) for message passing and communication. |
|
No message labeling but have to use diverse messages for different purposes. |
It defines messages properly and makes its discovery easy. |
Protocol Comparison
Message Format and Payload Handling
In a protocol comparison, MQTT employs a simple binary format comprising a topic and payload, enabling efficient data exchange between devices. The topic acts as an address for data routing, while the payload carries the transmitted data.
CoAP, in contrast, adopts a compact binary format with the option for CBOR encoding. This lightweight structure makes CoAP suitable for resource-constrained environments, ensuring efficient operation on devices with limited processing power and memory.
Quality of Service (QoS) Levels and Reliability
MQTT offers three levels of QoS to guarantee message delivery based on the application's requirements:
1. QoS level 0 (At most once): This level ensures best-effort message delivery, where messages are sent with no confirmation or acknowledgment from the recipient. Messages might be lost or duplicated, making it suitable for scenarios where occasional data loss is tolerable.
2. QoS level 1 (At least once): In this level, messages are guaranteed to be delivered at least once but might be duplicated. MQTT ensures message delivery by using acknowledgment packets and retransmissions if necessary. This level strikes a balance between reliability and overhead.
3. QoS level 2 (Exactly once): This is the highest level of reliability, ensuring that messages are delivered only once and without duplication. It achieves this by implementing a handshake mechanism and maintaining state information at both the sender and receiver sides. QoS level 2 is suitable for applications that require strict message delivery guarantees, such as critical infrastructure monitoring.
CoAP provides four different reliability modes for messages:
1. Confirmable (CON): Similar to MQTT's QoS level 1, CoAP's confirmable mode ensures that messages are acknowledged by the recipient. If a confirmation is not received, the message is retransmitted.
2. Non-confirmable (NON): This mode operates similarly to MQTT's QoS level 0, where messages are sent with no acknowledgment. There is no retransmission in case of non-acknowledgment, which reduces overhead.
3. Acknowledgment (ACK): This is a one-way communication mode, where only the presence of a message is acknowledged by the recipient, but no direct response is sent back. This mode is useful for notifications or status updates.
4. Reset (RST): The reset mode serves as a negative acknowledgment, indicating that a request is invalid or cannot be processed. This mode informs the sender that the request needs to be reformulated or abandoned.
Security Considerations
Ensuring the security of M2M communication in IoT environments is of paramount importance. Both MQTT and CoAP offer mechanisms to protect data and ensure secure communication.
MQTT Security
MQTT supports TLS (Transport Layer Security) encryption, providing confidentiality and data integrity during data transmission. TLS ensures that data exchanged between MQTT clients and brokers is encrypted, preventing unauthorized parties from intercepting and deciphering the information.
Furthermore, MQTT security includes mechanisms for client authentication and authorization. Clients can authenticate themselves to the broker using various methods such as username/password, X.509 certificates, or token-based authentication. The broker, in turn, can use access control lists (ACLs) to authorize specific clients to access certain topics or perform particular actions.
CoAP Security
CoAP, being designed for constrained devices in resource-limited environments, incorporates security features that are tailored to match its lightweight nature while ensuring secure communication.
1. DTLS (Datagram Transport Layer Security): CoAP relies on DTLS to provide a secure communication layer. DTLS is a lightweight version of TLS (Transport Layer Security) that operates over UDP, which is well-suited for low-power and lossy networks. DTLS adds a layer of encryption, authentication, and integrity checks to CoAP messages, safeguarding the data exchange between CoAP clients and servers.
2. Pre-Shared Keys (PSK) and Certificates: CoAP supports various authentication mechanisms, including Pre-Shared Keys (PSK) and X.509 certificates. PSK is suitable for resource-constrained devices as it requires less computational power for authentication. On the other hand, X.509 certificates provide stronger authentication and are more commonly used in large-scale deployments.
3. Message Encryption: DTLS ensures that CoAP messages are encrypted during transmission, preventing unauthorized parties from intercepting and reading the data. This encryption is particularly important when sensitive or private information is being exchanged between CoAP devices.
4. Secure Resource Access Control: CoAP servers can ensure secure resource access through access control policies. By implementing access control lists (ACLs), servers enforce fine-grained authorization, restricting specific resource access for authenticated clients and controlling their actions on those resources.
5. Caching and Forward Proxy Security: CoAP's built-in caching and forward proxy features should be configured with security considerations in mind. Caches should be protected from unauthorized access, and proxies should ensure secure and authenticated communication with both clients and servers.
6. Firewall and Network Security: As with any communication protocol, CoAP devices should be protected behind firewalls, and network security measures should be in place to prevent unauthorized access to CoAP devices and servers from the internet.
It's essential to acknowledge that CoAP offers security features, but their implementation level may differ based on device capabilities and application needs. In highly sensitive applications or large-scale deployments, additional security measures may be required to ensure maximum protection against potential threats and attacks.
Incorporating CoAP into an IoT system demands adherence to security best practices. Keeping devices and servers updated with the latest security patches and protocols is crucial to effectively tackle emerging security challenges. This proactive approach ensures a robust and secure deployment of CoAP in your IoT ecosystem.
Conclusion
In conclusion, both MQTT and CoAP are valuable M2M protocols for IoT applications. MQTT's lightweight and publish-subscribe model makes it versatile for various scenarios, while CoAP's design for constrained devices excels in low-power and lossy networks. The choice between the two depends on specific IoT use cases, with MQTT ideal for real-time monitoring and large-scale communication, and CoAP suitable for resource-constrained environments. As IoT evolves, ongoing research and advancements in M2M protocols will further optimize communication efficiency, security, and scalability. Selecting the right protocol, alongside considerations of security, network infrastructure, and data management, is vital for successful IoT deployments.